Entitlement and Security for Entra ID
Permission insights for Entra ID security and compliance

Entitlement and Security for Entra ID Features
Entra ID is Microsoft’s cloud-based identity and access management solution. It is a directory and identity management service that operates in Microsoft’s cloud environment and provides authentication and authorization services to Microsoft 365, Microsoft Azure, Dynamics 365, and various third-party services among others. It is a prime target for attackers that wish to gain or elevate privileges that could result in data breaches and service disruptions. Organizations need to verify the appropriate permissions are set and discover vulnerabilities and risky configurations to maintain security and operations.
Validate User Access
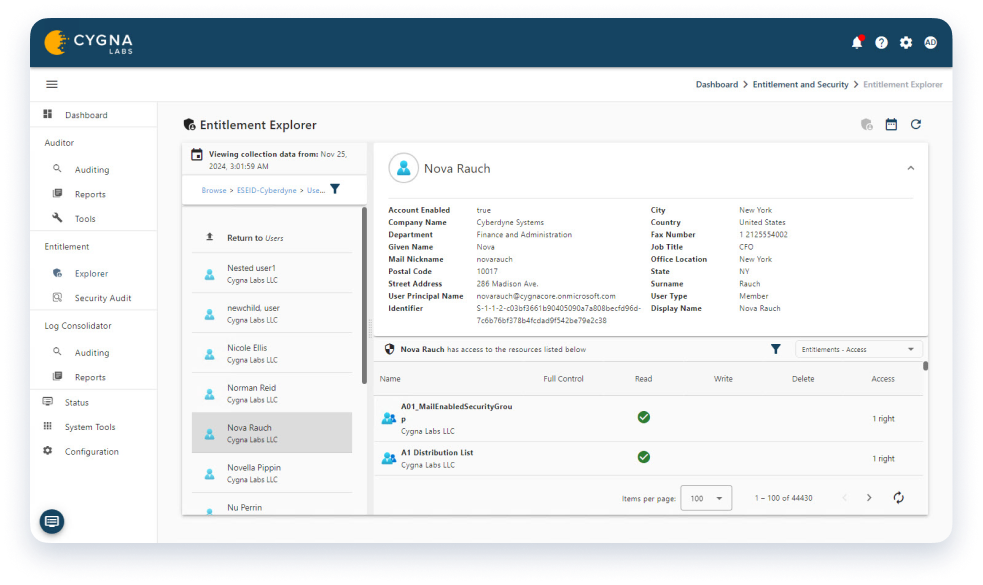
Examine entitlements to ensure that separation of duties and the principal least privilege is being followed. Verify permissions have been revoked when a user changes roles or leaves the organization.
Find High Risk Permissions and Settings
Locate potentially high-risk permissions in your environment. Find settings that could be giving broad access to sensitive resources or allowing unauthorised users to make permission changes.
Effective Permissions
Display the effective permissions to see directlyset and inherited rights. Expand to see alltrustees through group, role membership orconditional access policy. Verify that only thedesired users have the appropriate permissions.
Powerful Searching and Reporting
Search based on user access or permission perspectives using most recent or historical data. Built-in security audit reports provide answers to common important entitlement queries or easily create custom reports to suit your needs.

Take control of your systems today
Take the first step towards insight, alerts, and compliance on your audit data. Learn more by downloading a Cygna Auditor datasheet.
Download DatasheetRequest a Demo
Our experienced engineers will fine-tune the demo based on your specific needs. You’ll find out how easy it can be to secure your sensitive data.
Schedule a Demo